Dozens of malicious apps, some available in Play, found in the past couple months. Joker malware
September has been a busy month for malicious Android apps, with hundreds of them flooding either Google Play or third-party markets from a single malware family alone, researchers from security companies said.
Known as Joker, since late 2016, this family of malicious apps has been targeting Android users and has been one of the most common threats to Android more recently. Joker apps secretly subscribe to costly subscription services once activated and can even steal SMS messages, contact lists, and computer information. Researchers last July said they found Joker lurking about 500,000 times in 11 apparently legitimate apps downloaded from Play.
Late last week, researchers from security firm Zscaler said they discovered a new batch of 120,000 downloads containing 17 Joker-tainted games. Over the course of September, the applications were progressively uploaded to Play. Meanwhile, security firm Zimperium announced on Monday that in September, company researchers discovered 64 new Joker variants, most or all of which were seeded in third-party app stores.
(adsbygoogle = window.adsbygoogle || []).push({});And, as ZDNet noted, this month and in July, researchers from security firms Pradeo and Anquanke found more Joker outbreaks. Since it first came to light in December 2016, Anquanke said it had located more than 13,000 samples.
“Joker is one of the most prominent malware families that continually targets Android devices,” Zscaler researcher Viral Gandhi wrote in last week’s post. “Despite awareness of this particular malware, it keeps finding its way into Google’s official application market by employing changes in its code, execution methods, or payload-retrieving techniques.”
The roundabout way of attack is one of the keys to the Joker ‘s success. The apps are knockoffs of legitimate apps and contain no malicious code other than a “dropper” when downloaded from Play or a different market. The dropper, which is heavily obfuscated and includes only a few lines of code, installs a malicious part and drops it into the app after a delay of hours or even days.

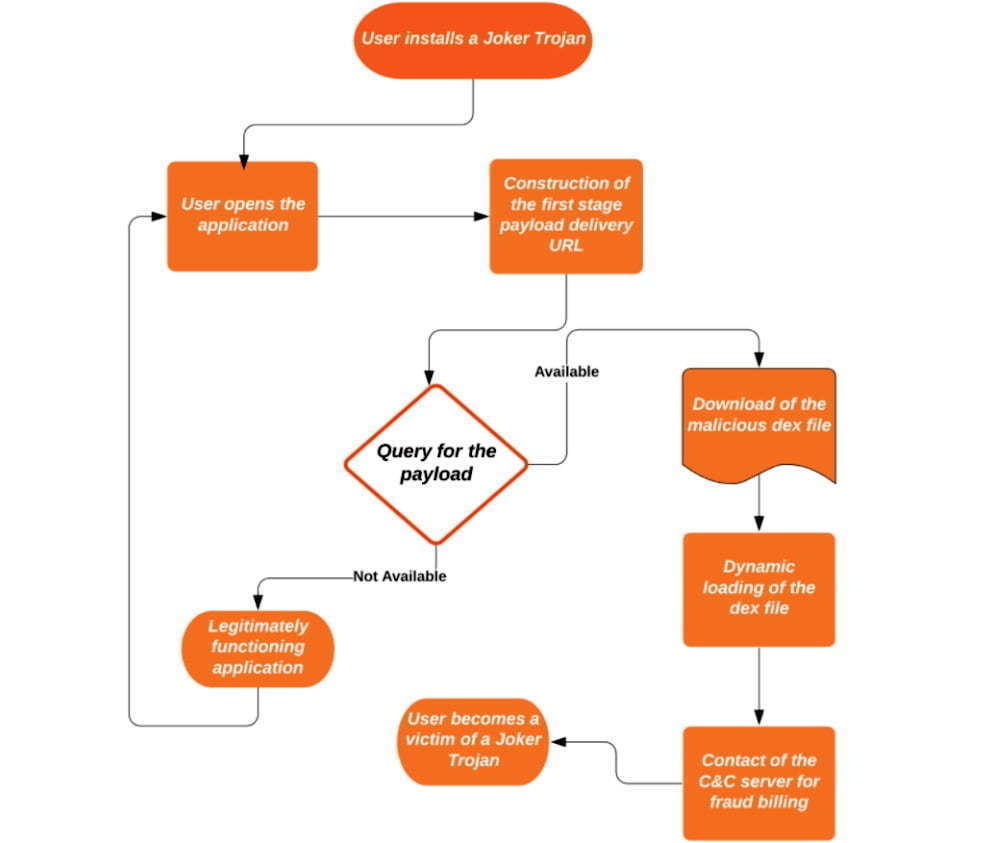
A flow chart that captures the four pivot points each Joker sample uses was given by Zimperium. In order to mask update components as innocuous applications such as games, wallpapers, messengers, translators and photo editors, the malware often uses evasion techniques.
(adsbygoogle = window.adsbygoogle || []).push({});The evasion techniques include encoded strings inside the samples where an app is to download a dex, which is an Android-native file that comprises the APK package, possibly along with other dexes. The dexes are disguised as mp3 .css, or .json files. To further hide, Joker uses code injection to hide among legitimate third-party packages—such as org.junit.internal, com.google.android.gms.dynamite, or com.unity3d.player.UnityProvider—already installed on the phone.
The purpose of this is to make it more difficult for the malware analyst to spot the malicious code, as third-party libraries generally contain a lot of code and the existence of additional obfuscation will make it much more difficult to spot the injected classes, “wrote Zimperium researcher Aazim Yaswant.” “In addition, the use of valid package names defeats naïve [blocklisting] attempts, but our z9 machine-learning engine allowed the researchers to detect the above-mentioned injection tricks safely.”
Three forms of post-download strategies to circumvent Google’s app-vetting process are detailed in the Zscaler write-up: direct downloads, one-stage downloads, and two-stage downloads. The final payload was the same, despite the delivery variations. If the final payload is downloaded and enabled by an application, the knock-off application has the opportunity to sign up for premium subscriptions using the user’s SMS app.
A Google spokesman declined to comment other than to note that Zscaler reported that the company removed the apps once they were privately reported.
(adsbygoogle = window.adsbygoogle || []).push({});Using an antivirus app from Malwarebytes, Eset, F-Secure, or another reputable maker is also an option, although they, too, can have difficulty detecting Joker or other malware.