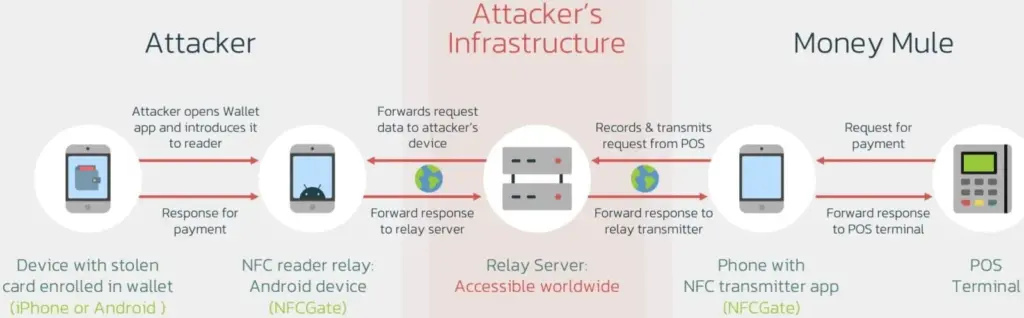
Cybercriminals have created a brand-new technique called “Ghost Tap,” which transmits NFC card information to money mules all around the world, to profit from stolen credit card information connected to mobile payment systems like Apple Pay and Google Pay.
The strategy expands on techniques used by mobile viruses such as NGate, which were reported by ESET in August and involved using payment card Near Field Communication (NFC) signals. Ghost Tap employs money mules at several remote places connecting with Point of Sale (PoS) terminals, is more obfuscated and difficult to detect, and does not require the victim’s mobile or card. It also does not require constant victim interchange.

Ghost Tap was found by mobile security company Threat Fabric, which cautions about the growing potential and adoption of the novel method. Threat Fabric told Droid Tools that it has recently observed an increase in the use of Ghost Tap in the field.
An overview of Ghost Tap and a comparison with NGate
The attack starts by stealing payment card information and intercepting the one-time passwords (OTP) required to register for a virtual wallet on Google Pay and Apple Pay. Payment card information can be stolen via phishing websites, keylogging, or banking malware that shows overlays that seem like digital payment apps.
Malware that tracks text messages or social engineering are two ways that OTPs can be stolen. Previously, NGate-based assaults required the use of specialist software to mislead the victim into scanning their card via the NFC mechanism on their device.
Payment card information is still transmitted using the NFCGate tool. But in the interim, a relay server is set up to transmit the information to a vast network of money mules while hiding their true locations. Using the NFC chip on their cellphone, the mules then make large-scale, multi-location retail purchases, making it challenging to identify the main attacker or map the fraud network.
Threat actors were restricted to making minor contactless payments and ATM withdrawals during the NGate attacks, which jeopardized their identity and occasionally resulted in arrests.
The threat actors have stopped making ATM withdrawals as a result of the new Ghost Taps operation. Rather, they merely carry out cash outs at the time of sale and distribute them around a vast global network of mules. This just endangers the mules by obscuring the path to the primary perpetrators of the nefarious conduct.
Defending Against Ghost Tap
Threat Fabric cautions that because the transactions seem authentic and take place across several locations, the new strategy is difficult for financial institutions to identify and halt.
The researchers claim that although many banks’ anti-fraud systems identify purchases made in odd places, as when visiting another nation, the many tiny payments might evade these detections.
“The new tactic for cash-outs poses a challenge for financial organisations: the ability of cybercriminals to scale the fraudulent offline purchases, making multiple small payments in different places, might not trigger the anti-fraud mechanisms and might allow cybercriminals to successfully buy goods that can be further re-sold (like gift cards),” explains ThreatFabric.
If the attack is used widely, the total amount lost might be substantial even though all of these tiny transactions seem to have originated from the same device (connected to the same Apple Pay or Google Pay account). The mules switched their handsets to “airplane mode,” which still permits the NFC system to operate normally, in order to avoid being tracked.
Banks may only prevent Ghost Tap by flagging transactions made using the same card at locations that are physically impossible to visit in between charges. For instance, carrying out a fraudulent transaction in Cyprus 10 minutes after completing one in New York.
From the standpoint of the customer, keeping an eye out for fraudulent transactions and promptly reporting them to your bank is essential for freezing the card and reducing losses.