Using a warning to backup the key to prevent losing access, a recently identified Android malware known as Crocodilus deceives users into entering the seed phrase for the bitcoin wallet.
Despite being a recent banking malware, Crocodilus has fully functional capabilities to remotely control, take over the device, and collect data.
According to researchers at the fraud prevention firm ThreatFabric, the malware is disseminated by a custom dropper that gets around security measures in Android 13 and later.
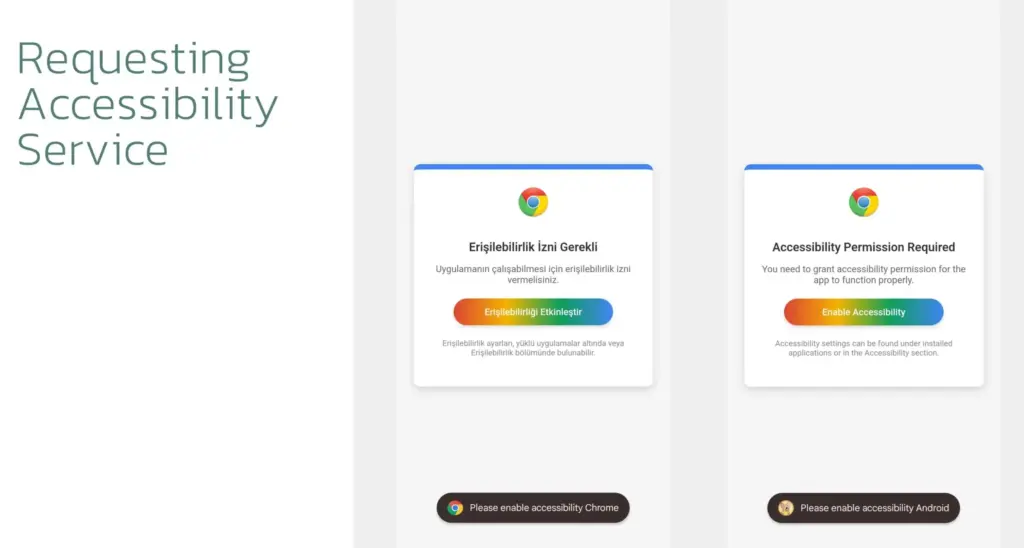
The dropper circumvents Accessibility Service limitations and installs the virus without activating Play Protect.
Crocodilus is unique because it uses social engineering to force victims to divulge their crypto-wallet seed phrase.
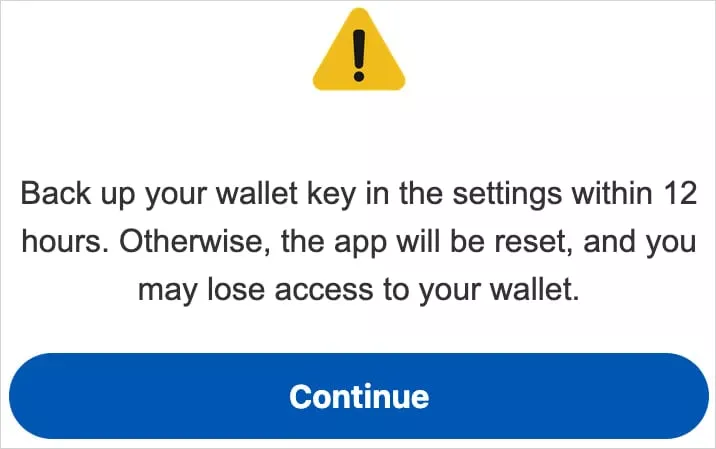
A screen overlay alerting users to “back up their wallet key in the settings within 12 hours” or risk losing your wallet is how it accomplishes this.
“This social engineering trick guides the victim to navigate to their seed phrase (wallet key), allowing Crocodilus to harvest the text using its Accessibility Logger,” ThreatFabric explains.
“With this information, attackers can seize full control of the wallet and drain it completely,” the researchers say.
Crocodilus was seen to target customers in Spain and Turkey, including bank accounts from those two nations, during its initial operations. Based on the debug messages, it seems that the infection originated in Turkey.
Although the exact mechanism of the first infection is unknown, users are usually duped into downloading droppers by malicious websites, phony SMS or social media advertisements, and third-party app shops.
When Crocodilus is launched, it has access to Accessibility Services, which are typically designated for helping individuals with disabilities. These services allow Crocodilus to make navigation motions, monitor for app launches, and unlock screen content.
Crocodilus puts a phony overlay over the legitimate app when the victim accesses a targeted banking or cryptocurrency app in order to obtain the victim’s login information.
The bot component of the malware supports a set of 23 commands that it can execute on the device, including:
- Enable call forwarding
- Launch a specific application
- Post a push notification
- Send SMS to all contacts or a specified number
- Get SMS messages
- Request Device Admin privileges
- Enable a black overlay
- Enable/disable sound
- Lock screen
- Make itself the default SMS manager
Additionally, the malware has remote access trojan (RAT) capabilities that let its operators swipe, tap, and browse the user interface, among other things.
To collect one-time password codes used for two-factor authentication account protection, a specific RAT command is also available to snap a screenshot of the Google Authenticator application.
To conceal the activity from the victim and give the impression that the device is locked, Crocodilus operators can mute the device and activate a black screen overlay while doing these tasks.
Crocodilus may soon expand its activities and add more apps to its target list, even if it currently seems to be targeting only Spain and Turkey.
It is recommended that Android users make sure Play Protect is constantly enabled on their devices and refrain from downloading APKs from sources other than Google Play.