According to a survey by cloud security firm Zscaler, hundreds of malicious Android apps on Google Play were downloaded over 40 million times between June 2024 and May 2025.
The company saw a 67% year-over-year increase in malware that targeted mobile devices during that time, with banking trojans and spyware being the most common threats.
According to telemetry data, threat actors are leveraging phishing, smishing, SIM-swapping, and payment frauds to take advantage of mobile payments instead of traditional card fraud.
The shift to social engineering assaults can be explained by the widespread use of mobile payments and enhanced security standards like chip-and-PIN technology.
According to Zscaler, “to carry out these assaults, fraudsters use phishing trojans and malicious programs designed to steal financial information and login passwords.”
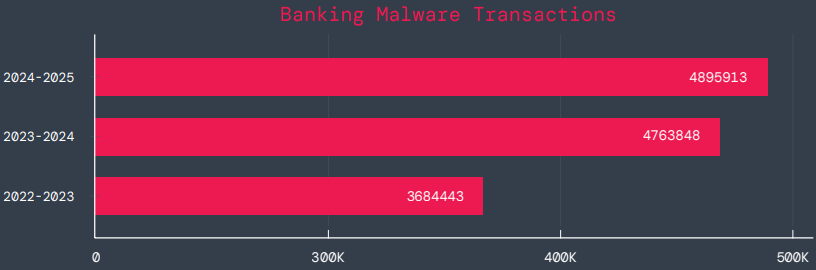
Zscaler estimates that it has found 239 harmful apps in the official Android store, with a total of 42 million downloads, compared to 200 malware apps on Google Play last year.
The emergence of adware as the most significant threat in the Android ecosystem, which now accounts for over 69% of all detections—nearly twice as many as the previous year—is another noteworthy trend observed at that time.
After leading with 38% the previous year, the Joker info-stealer is currently in second position with 23%.
The SpyNote, SpyLoan, and BadBazaar families—which are used for identity theft, extortion, and surveillance—were the primary drivers of the notable 220% year-over-year (YoY) increase in spyware.
Geographically speaking, 55% of all attacks were directed towards the United States, Canada, and India. Attacks against Israel and Italy also showed substantial increases, ranging from 800% to 4000% YoY, according to Zscaler.
Malicious Android apps and malware
In its annual study, Zscaler identifies three malware families that significantly affected Android users. The first is Anatsa, a banking trojan that occasionally enters Google Play through productivity and utility apps and receives hundreds of thousands of downloads each time.
Since its discovery in 2020, anatsa has undergone continuous evolution. The most recent version is capable of stealing data from bitcoin sites, more than 831 financial institutions, and new areas like South Korea and Germany.
The second is Android Void (Vo1d), a backdoor malware that targets Android TV boxes and has infected at least 1.6 million devices with out-of-date Android Open Source Project (AOSP) versions, mostly in Brazil and India.
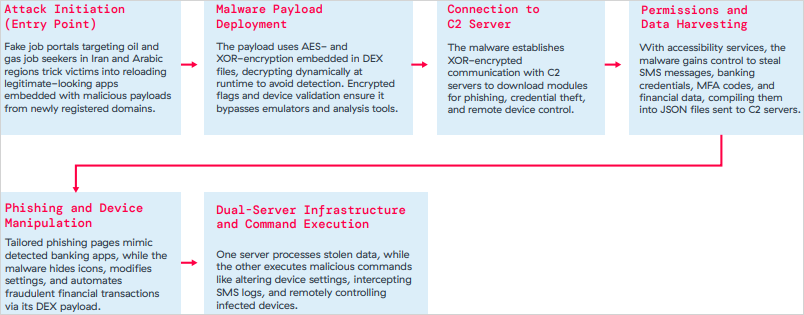
The third is Xnotice, a brand-new Android remote access trojan (RAT) that specifically targets job seekers in the oil and gas sector in Iran and Arabic-speaking areas.
Xnotice propagates via applications that are disseminated through phony employment websites and pose as tools for registering for exams or applying for jobs.
Through overlays, multi-factor authentication (MFA) codes, SMS messages, and screenshots, the spyware targets banking credentials.
Users are encouraged to install security updates, only trust reliable publishers, reject or restrict accessibility permissions, refrain from downloading unnecessary apps, and routinely run Play Protect scans in order to protect themselves from Android malware threats, including those from Google Play.
Routers continued to be the most targeted IoT equipment this year, according to Zscaler’s study. Hackers added routers to botnets or used them as proxies to spread malware by taking advantage of command injection flaws.
The majority of IoT attacks took place in the United States, with rising hotbeds in Hong Kong, Germany, India, and China following, suggesting that attackers are targeting devices throughout a larger geographic area.
The cybersecurity company advises businesses to harden IoT and cellular gateways by keeping an eye out for anomalies and implementing firmware-level protections, as well as to deploy zero-trust solutions for key networks.
Strict application control guidelines, security against phishing attacks, and monitoring SIM-level communications for anomalies should all be part of mobile endpoint protections.











